Top Remote Office Solutions for Multi-Location Companies: A Complete Guide
As businesses expand across multiple offices, cities, or states, managing technology becomes increasingly complex. For Houston-area small and midsized businesses, supporting multi-location, remote, and hybrid teams now require more than basic IT support. Today’s organizations must compare remote office solutions that unify remote IT infrastructure, cloud-based office systems, virtual desktop solutions, remote network management, and…
How Remote Office Solutions Are Transforming Modern Businesses in 2026
The way businesses operate has fundamentally changed—and by 2026, remote and hybrid work environments are no longer optional. They are a strategic requirement. For small to midsized businesses, especially those competing in fast-moving markets, the ability to Support remote office solutions reliably and securely has become a defining factor in productivity, resilience, and growth. Modern…
Remote Monitoring: Empowering Houston Business Operations
Overview: The Importance of Remote Monitoring Solutions Houston businesses are facing increased demand for secure, reliable, and scalable IT systems. Remote monitoring solutions give local organizations real-time visibility into network performance, device health, and potential threats. With the right tools in place, businesses can reduce downtime, boost productivity, and focus on core growth initiatives. …
Network Support and Operations: Connecting Houston
Network Support Needs for Houston Businesses Houston businesses depend on reliable, secure networks to thrive in today’s digital marketplace. When connectivity falters, it can mean lost revenue, productivity, and customer trust. That’s why partnering with top network support companies is essential to keep operations running smoothly and securely. The Role of Network Support Companies Network…
Why Your Houston Business Needs More Than Just IT Support
Houston’s fast-growing businesses face a complex landscape: digital transformation, cybersecurity risks, remote work, and ever-changing technology. To thrive, you need more than simple tech support—you need a full-spectrum IT partner that can plan, implement, and manage your technology from strategy to day-to-day support. That’s where Crescent IT Systems comes in, offering everything from IT strategy…
Maximizing Value: Consulting Services IT Solutions for Growth
Introduction: The Value of Consulting Services IT for Growth In Houston’s competitive landscape, businesses need more than just technology—they need consulting services IT that drive measurable growth. The right partner can turn technology investments into real business results, offering both immediate improvements and long-term gains. Consulting Services vs. IT Consulting Business: Finding the Right Fit…
Cloud and Technical IT Consulting Explained
Cloud and technical IT consulting have become essential for Houston enterprises seeking to stay agile, secure, and competitive. As digital transformation accelerates, businesses need more than just traditional IT support—they need specialized guidance from a trusted it services company that understands both cloud and technical landscapes. The Importance of Technical IT Consulting in Today’s Market…
Remote Office Solutions for Safer & Flexible Business
Security Challenges in Remote Office Environments Houston businesses are facing an unprecedented shift toward remote and hybrid work. This change brings new security challenges—requiring robust Remote Office Solutions to protect sensitive data, prevent cyberattacks, and ensure smooth business operations no matter where your team works. The Role of Remote IT Support in Mitigating Risks Remote…
Maximizing IT Performance with RMM and Desktop Monitoring
The Rise of RMM Remote Management in Houston Businesses in Houston are increasingly relying on advanced RMM remote management to keep their IT systems secure, efficient, and scalable. As threats grow and operations become more complex, having reliable remote monitoring and management solutions is now essential for maintaining business continuity and driving growth. Remote Desktop…
Building a Secure and Productive Remote Office in Houston
Why Houston Businesses Are Switching to Managed IT Services Houston’s fast-growing business scene depends on reliable, secure, and scalable technology. Increasingly, companies across Houston are choosing managed IT services to stay ahead of the curve, minimize downtime, and ensure business continuity. The Rise of Remote Work in Houston Remote work is transforming how Houston businesses…
Essential Guide to Remote Office Solutions for Modern Businesses
Why Remote Office Solutions Matter in Today’s Business World Houston businesses are rapidly embracing Remote Office Solutions to stay agile and competitive in a changing workplace. Whether supporting hybrid teams or enabling full remote work, these solutions deliver the flexibility, security, and collaboration modern businesses need to thrive. Understanding Remote IT Support: Keeping Teams Productive…
Optimizing IT with Advanced RMM and Remote Monitoring
Understanding RMM Solutions for Modern IT For Houston businesses, maintaining IT performance is crucial in today’s digital world. An RMM solution (Remote Monitoring and Management) provides centralized tools to monitor, maintain, and manage network devices, servers, and endpoints—keeping your operations secure and efficient. The Role of Remote System and Network Monitors A remote system monitor…
Remote Monitoring & Management for Houston Businesses 24/7
Why Remote Monitoring Matters for Houston Organizations For Houston businesses, staying connected and secure is essential. Remote monitoring provides the oversight needed to maintain operational continuity, protect sensitive data, and address potential issues before they disrupt daily operations. By leveraging advanced remote monitoring and management, organizations gain the confidence that their IT infrastructure is always…
Remote Monitoring for Houston: Boosting Business Performance
The Evolution of Remote Monitoring Systems Houston businesses operate in a fast-paced environment where system uptime and security are non-negotiable. Modern remote monitoring systems have evolved from basic oversight tools to advanced platforms that deliver real-time insights, proactive alerts, and automated maintenance—empowering local companies to stay ahead of IT challenges. Exploring Remote Monitoring Services and…
Advanced Strategies in Cloud-Based Backup & Disaster Recovery
Advanced Strategies in Cloud-Based Backup & Disaster Recovery Introduction: Cloud Computing Backup and Recovery Trends in Houston Houston businesses are turning to cloud computing backup and recovery as a cornerstone of their data protection strategies. With rising threats and compliance demands, adopting advanced backup and disaster recovery solutions ensures companies remain resilient, no matter the…
The Essentials of Backup & Disaster Recovery for Houston Businesses
The Essentials of Backup & Disaster Recovery for Houston Businesses Why Backup & Disaster Recovery Matters for Houston Companies In Houston’s fast-paced business environment, backup & disaster recovery isn’t optional—it’s essential. Companies must protect their critical data and systems from threats like cyberattacks, hardware failure, and severe weather. Without a robust backup and disaster recovery…
Data Backup & Recovery Planning for Modern Enterprises
Advanced Strategies in Cloud-Based Backup & Disaster Recovery Introduction: Cloud Computing Backup and Recovery Trends in Houston Houston businesses are turning to cloud computing backup and recovery as a cornerstone of their data protection strategies. With rising threats and compliance demands, adopting advanced backup and disaster recovery solutions ensures companies remain resilient, no matter the…
Cloud Backup Solutions for Complete Business Continuity
Cloud Backup Solutions for Complete Business Continuity Why the Backup and Disaster Recovery Process Matters For Houston businesses, the backup and disaster recovery process is the foundation of business continuity. In a city prone to storms, outages, and cyber threats, robust planning ensures your company can restore operations quickly and avoid costly downtime. Choosing the…
Disaster Recovery Procedures Every Business Should Know
Disaster Recovery Procedures Every Business Should Know Introduction: Understanding Disaster Data Recovery in Houston Disaster data recovery is a must for Houston businesses facing everything from hurricanes to cyberattacks. Having robust plans and reliable cloud backup and recovery services ensures your critical data is always protected and quickly restored, keeping your business running no matter…
Choosing the Right IT Cloud Solutions for Houston Businesses
Introduction: Why Houston Businesses Need IT Cloud Solutions In today’s competitive market, Houston companies need agile, reliable, and secure IT cloud solutions to thrive. From cost savings to enhanced security, the right cloud approach unlocks growth opportunities for businesses of all sizes. Exploring the Latest Computing Cloud Services Modern computing cloud services offer flexible, on-demand…
Comprehensive Cloud Services for Houston Businesses
What Does “Cloud Computing Cloud Computing” Mean? Cloud computing cloud computing refers to leveraging multiple cloud platforms and environments together, allowing Houston businesses to access, manage, and store data flexibly and securely. With this approach, you gain unmatched scalability, improved collaboration, and the ability to rapidly adapt IT resources as your business grows. The…
Houston Cloud Services Simplified
Understanding Cloud Computing and Cloud Services Cloud computing and cloud services are reshaping the way Houston businesses operate, offering unprecedented flexibility, efficiency, and security. With the right cloud solutions, organizations can reduce costs, streamline operations, and stay agile in a fast-changing marketplace. Leveraging Cloud to Cloud Integrations for Flexibility Cloud to cloud integrations connect multiple…
Navigating the Cloud: Solutions for Every Stage of Growth
Demystifying “Cloud” in Today’s Business IT Cloud technology has become central to modern Houston businesses. By embracing the cloud, organizations access scalable, secure resources, reduce IT overhead, and future-proof operations for growth. The Relationship Between Cloud and Cloud Computing Cloud and cloud computing are often used interchangeably, but there are distinctions. The cloud refers to…
Cloud Security Solutions for Houston Businesses
Importance of Security and Cloud Computing in Houston For Houston businesses, safeguarding data and ensuring uninterrupted operations is more critical than ever. Security and cloud computing are now essential elements of modern IT strategies—offering scalable, real-time protection against cyber threats and disasters. By embracing cloud-powered security, companies achieve stronger defense, faster recovery, and regulatory compliance.…
Maximizing Security: Managed Cyber Security Solutions
Maximizing Security: Managed Cyber Security Solutions The Rise of Cyber Threats in Houston Cyber threats are increasing rapidly in Houston, putting local businesses at risk of data breaches, ransomware, and costly downtime. Modern organizations need more than just basic network protection—managed cyber security services are essential for safeguarding business continuity and customer trust. What Are…
Essential Managed Network Services for Houston
Essential Managed Network Services for Houston Why Managed Network Services Matter in Houston In today’s fast-paced Houston business environment, reliable and secure network infrastructure is essential. Managed network services empower local businesses to maintain peak performance, ensure network security, and adapt to changing demands—all while reducing costs and IT headaches. What Is a Managed Network?…
Building Secure Cloud and Hybrid Networks in Houston
Building Secure Cloud and Hybrid Networks in Houston The Need for Cloud and Hybrid Network Solutions In today’s fast-evolving digital landscape, Houston businesses require flexible, secure, and reliable network infrastructure to stay competitive. Cloud network services and hybrid network models provide scalable solutions that support business continuity, protect sensitive data, and empower your team no…
Next-Gen Networking for Business Growth
The Evolving IT and Network Services Landscape In Houston’s rapidly evolving digital landscape, having reliable IT network services is essential for staying ahead. As companies shift to hybrid work and cloud-based operations, modern IT and network services deliver connectivity, security, and scalability Houston businesses need to grow with confidence. Benefits of IT Network Services for…
Why Houston Businesses Are Switching to Managed IT Services
Houston’s fast-growing business scene depends on reliable, secure, and scalable technology. Increasingly, companies across Houston are choosing managed IT services to stay ahead of the curve, minimize downtime, and ensure business continuity. What Are Managed IT Services? Managed IT services are comprehensive solutions provided by an external partner, covering everything from cybersecurity and data backup…
How IT Consulting Companies Drive Digital Transformation in Houston
Houston’s business landscape is evolving rapidly, and having the right IT consulting partner is more critical than ever. With technology shaping every aspect of business, local companies need trusted guidance to stay competitive, secure, and agile. Introduction: Why IT Consulting Is Essential for Houston Businesses For more than 30 years, Crescent IT Systems has helped…
The Complete Guide to IT Consulting Services for Houston Businesses
Houston’s business landscape is evolving rapidly, and having the right IT consulting partner is more critical than ever. With technology shaping every aspect of business, local companies need trusted guidance to stay competitive, secure, and agile. Introduction: Why IT Consulting Is Essential for Houston Businesses For more than 30 years, Crescent IT Systems has helped…
Flexible IT Solutions—The Power of Managed Services and Support in Houston
Flexible IT Solutions—The Power of Managed Services and Support in Houston Flexibility is key in today’s dynamic Houston business environment. Whether you’re scaling up, navigating industry regulations, or shifting to remote work, managed IT support services provide the adaptability modern organizations need to thrive. Why Flexibility Matters for Houston Businesses As your business changes, so…
Maximizing Business Security with IT Support Managed Services
Maximizing Business Security with IT Support Managed Services Houston’s business community is increasingly targeted by cybercriminals and data breaches. To protect sensitive information and ensure business continuity, more organizations are investing in IT support managed services for comprehensive, proactive security. Cybersecurity Threats Facing Houston Businesses From ransomware attacks to phishing scams, the threats facing Houston…
How to Choose the Right Managed Service IT Provider in Houston
How to Choose the Right Managed Service IT Provider in Houston Finding the right managed service IT provider is one of the most important decisions your Houston business can make. The right provider offers not just technical expertise, but local insight, fast response times, and the ability to scale as your business grows. The Importance…
Why Houston Businesses Are Switching to Managed IT Services
Why Houston Businesses Are Switching to Managed IT Services Houston’s fast-growing business scene depends on reliable, secure, and scalable technology. Increasingly, companies across Houston are choosing managed IT services to stay ahead of the curve, minimize downtime, and ensure business continuity. What Are Managed IT Services? Managed IT services are comprehensive solutions provided by an…
The Complete Guide to Managed IT Services for Houston Businesses
In Houston’s fast-changing business environment, companies of all sizes rely on managed IT services to power operations, protect data, and drive growth. This guide explains what managed IT services are, how they work, and why partnering with a local expert like Crescent IT Systems gives your business a real advantage. What Are Managed IT Services?…
The Fundamentals of Cybersecurity for Houston Businesses
In today’s digital world, Houston businesses of all sizes face a constant barrage of cyber threats. Understanding the basics of cybersecurity is essential for safeguarding sensitive data, customer trust, and business continuity. Why Cybersecurity Matters for Houston Businesses Cyber attacks in Houston are on the rise, targeting everyone from small startups to major enterprises. Partnering…
Building a Strong Network Security Foundation
Building a Strong Network Security Foundation Houston’s thriving business sector is a top target for cybercriminals. With sensitive data, client information, and financial assets at stake, a robust network security strategy is critical for organizations of all sizes. Introduction: Network Security Risks Facing Houston Organizations Local businesses in Houston are constantly challenged by new cyber…
Advanced Cybersecurity Services and Solutions
Advanced Cyber Security Services and Solutions As Houston’s digital landscape expands, so do the risks. To stay ahead of evolving cyber threats, more organizations are turning to advanced cybersecurity services that offer expert support, powerful technologies, and proactive strategies. Introduction: When to Seek Advanced Cybersecurity Services in Houston Businesses in Houston face constant cyber risks—from…
The Rise of Cloud Security in Modern Business
The Rise of Cloud Security in Modern Business Houston’s business landscape is evolving fast, and cloud technology is at the heart of this transformation. But as more organizations move their operations to the cloud, cloud network security has never been more critical. Introduction: Why Cloud Security Is Critical for Houston Enterprises Cyber threats target businesses…
Practical Strategies for Business-Wide Security
Practical Strategies for Business-Wide Security Houston’s organizations face unprecedented cyber risks—from phishing scams to ransomware and insider threats. To protect your business, you need a comprehensive plan for cyber security; security that covers every department and endpoint. Introduction: Defining Cyber Security in Today’s World Cyber security today goes far beyond firewalls and antivirus. It means…
Cybersecurity Best Practices for CPAs in 2025
Cybersecurity Best Practices for CPAs in 2025 In 2025, cybersecurity for accounting firms is not just important—it’s essential. As accounting firms handle a wealth of sensitive financial data, they have become prime targets for cyberattacks. Why is cybersecurity essential? Cybercriminals seek access to tax records, payroll information, and banking credentials, which can be exploited for…
IT Support for Small Business Owners: A 10-Step Survival Guide
IT Support for Small Business Owners: A 10-Step Survival Guide Modern small businesses face increasingly complex technological demands. Having the right IT support isn’t just convenient, it’s essential. Whether you’re a startup or a growing company in Houston, here’s a 10-step survival guide designed to help you gain control of your systems and ensure operational…
The Best Password Managers of 2025: Secure Your Digital World with Confidence
The Best Password Managers of 2025: Secure Your Digital World with Confidence As cyber threats grow more sophisticated and online accounts multiply, managing and protecting your passwords is no longer optional—it’s essential. In 2025, choosing the best password manager 2025 means more than just remembering logins; it’s about securing your identity, improving productivity, and protecting…
Ensuring Your Law Firm’s IT Meets Texas Compliance Standards
Introduction: IT Compliance Is Both a Shield and a Growth Engine IT compliance is no longer a box‑ticking exercise for Texas law firms. It is a strategic imperative that: Safeguards Client Trust – Demonstrating robust cybersecurity reassures clients that their privileged information is protected. Protects Your Reputation – Compliance proves you take ethical obligations seriously,…
Cybersecurity Tips for Houston Businesses: Protect Your Data in 2025
The Growing Importance of Cybersecurity in Houston In today’s digital-first economy, cybersecurity isn’t just an IT issue, it’s a core business concern. Houston, as a rapidly growing business hub, is seeing increased cyber threats targeted specifically at small to midsize businesses. Without robust cybersecurity measures, companies risk data breaches, financial loss, and severe damage to…
Why Flexibility in IT Support is Crucial in Uncertain Economic Times
Introduction In today’s rapidly changing economy, small to mid-sized enterprises (SMEs) face unique challenges, making the adaptability of IT support crucial. This post highlights how scalable and customized IT solutions are key to helping businesses thrive amidst economic fluctuations. Why is Flexibility Important in IT Services? Importance of Scalable IT Services Scalable IT services, which…
7 Crucial IT Strategies for Economic Uncertainty: Unleashing Your SMB’s Potential
In the face of economic uncertainty, small and medium-sized businesses (SMBs) must take proactive measures to fine-tune their IT operations and maximize their financial performance. “On the economy, 52% of small business owners said they believe the economy is already in a recession the survey found.” -Reuters.com To position your business for success and thrive…
The Essential IT Tips to Know Before Moving Your Company to a New Location
The Essential IT Tips to Know Before Moving Your Company to a New Location Introduction A move can be a stressful time for any company, but it’s even more so when you’re dealing with computers and technology. In this guide we will give you some essential IT tips to keep in mind before moving your…
How to Build Your Cybersecurity Incident Response Plan
How to Build Your Cybersecurity Incident Response Plan When a cyberattack strikes, how fast can you respond? Ransomware attacks are up threefold in 2021. A recent NCC group reports that the number of ransomware attacks analyzed by the team has increased by 288% between January-March 2021 and April-June 2021. Cybersecurity risks are out there…
Best Practices to Prevent Ransomware
According to Cybersecurity Ventures, it states that there will be a ransomware attack on businesses every 11 seconds in 2021. This does not include attacks on individuals, which occur even more frequently than businesses. Businesses need to act now to shore up their cybersecurity to protect themselves from cyberattacks. What is Ransomware? Ransomware is a…
7 Best Work-From-Home Security Practices
COVID-19 has affected almost every business in 2020, forcing companies to send some, most, or all their employees to work from home with the COVID-19 shutdown mandate. The hasty transition from on-premises to off-premises work has all but thrown out the company’s IT playbook, and the level of security found in the employee’s home offices…
Virus Now Has Evolved to Spread Through the Wi-Fi Like a Worm
Virus Now Has Evolved to Spread Through the Wi-Fi Like a Worm Security Alert from Crescent IT Systems The ThreatPost.com reported that a virus seen as a banking trojan in 2014 has evolved over the years and recently has returned as a extremely dangerous malware delivery system. The Emotet malware has returned with the ability…
Cybersecurity: Protecting Your Small Business from Cyber Crime
Small businesses are considered a rich targets for cybercrime today. James Morrison, a Houston FBI Computer Scientist, speaking about Cybersecurity at the West Houston Chamber Cybersecurity event on August 2nd framed the danger to businesses today. Morrison stated, “The mindset of the cyber criminals is different than normally think. It is not what they can steal…
Ransomware Attacks Grow with Better Hacker Tools
Ransomware Attacks Grow with Better Hacker Tools As little as a few years ago the tools in use were only dreamed about in deploying and loading the ransomware “cannons”. But with the availability of sophisticated hacker tools, especially the ransomware tools on the dark net, anyone can deploy a ransomware attack. Businesses today need a…
Fastest VPNs of 2019 – Our top 5 for speed
A VPN’s primary purpose is to ensure privacy and security online, but no one wants to compromise speed. High speed is always a top priority for those shopping for a VPN service, and many providers have laid claim to the title of the world’s fastest VPN. All VPNs slow down your internet to some degree,…
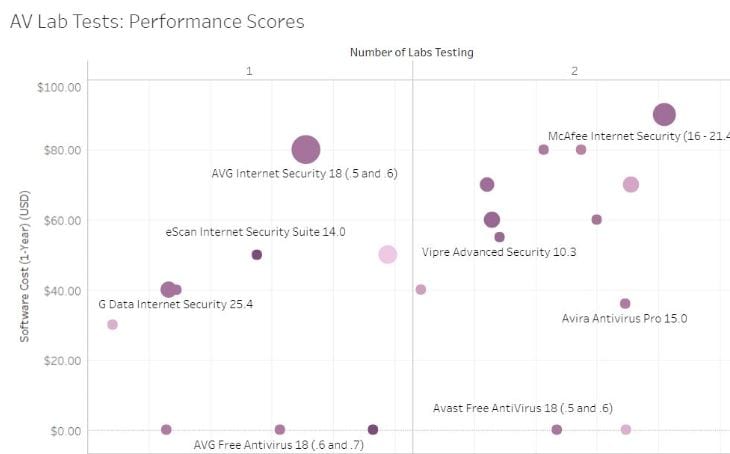
The ultimate data driven antivirus comparison
Using independent antivirus lab test results and website review scores, we charted and compared top AV tools based on multiple points, including overall protection, system performance, false positives, price, and more. There are currently dozens of antivirus tools available on the market. Big name options such as Norton, McAfee, Bitdefender, and AVG typically get the…
Apple appears to have blocked GrayKey iPhone hacking tool Apple and two companies that have worked to enable iPhone de-encryption continue their back-and-forth efforts.
Apple has apparently been able to permanently block de-encryption technology from a mysterious Atlanta-based company whose blackbox device was embraced by government agencies to bypass iPhone passcodes.
Make 2018 your year of taking password security more seriously
The popularity of passwords as a means of authentication is still not waning, so advice on how to opt for passwords that are hard to guess and crack is always timely Choosing passwords For one, avoid the most often used passwords. SplashData’s most recent list of the top 100 worst passwords (of the past year)…
7 Tips to Improve Data Backup and Ensure Business Continuity
Improving backup and continuity is frequently listed as a top five priority for IT organizations, but for many organizations, backup and recovery processes need to improve a lot, not just incrementally. Today, enterprises often run backup tools, and rely on business continuity processes, designed for older platforms developed before elastic clouds, near-ubiquitous virtualized workloads, or…
IT buyer’s guide to business laptops
Business-friendly notebooks come in all shapes, sizes and prices. Here’s help picking the laptops best suited to your organization’s various employees. With hundreds of business-oriented laptops to choose from — everything from sleek ultralight tablets to huge portable workstations — picking the right ones to outfit your company’s workforce can make finding a needle in…
Prioritizing Your Security – Where Do You Begin?
There are two key trends happening in today’s networks the c-suite executives need to be paying close attention to. The first is that IT teams are struggling to keep up with digital transformation demands, including the move to multi-cloud infrastructures and services, the rapid adoption of IoT networks and devices, BYOD and a highly mobile…
Don’t be the fool in the cloud
Is it really that hard to keep from making a security idiot of yourself? When I hear people worrying about cloud security, they’re usually shaking in their boots about some obscure bug beyond their control. Ha! Ordinary, stupid human mistakes are more than bad enough. For example, Accenture left hundreds of gigabytes of private user…
Facebook doesn’t listen through your phone’s mic — except when it does
Facebook denies listening to your conversations to target advertising. But denial wording seems odd. Credit: U.S. Navy, via Celestial Images [public domain] Is Facebook listening to every word you say? Zuck’s crew says it won’t use your speech to target advertising or reorder your feed, but it’s still unclear what it does use the microphone…
The Best Password Managers of 2017
Everyone Needs a Password Manager This year, World Password Day falls on Star Wars Day. May the fourth be with you! Celebrate by changing all your simple passwords to strong ones, with different ones for every secure site. If that doesn’t sound like fun, consider getting some help. First, install a password manager. Second, get…
How to avoid ransomware attacks: 10 tips
As ransomware increasingly targets healthcare organizations, schools and government agencies, security experts offer advice to help IT leaders prepare and protect. Biometrics and Fingerprint Scan Security Technology Concept Nigerian princes are no longer the only menaces lurking in an employee’s inbox. For healthcare organizations, schools, government agencies and many businesses, ransomware attacks—an especially sinister type…
4 Big Updates Coming to Windows 10 This Summer
Source: PC Mag – Michael Muchmore After last year’s big splashes with Windows 10 and HoloLens, this year’s Microsoft Build was more incremental. Though Microsoft didn’t release or announce a new version of Windows at the event, or even any new hardware, it did give us a look at what’s coming up in the…
How to Get Google to Quit Tracking You
How to Get Google Maps to Stop Following You Where you go, Google goes. If you have location services turned on, then Google Maps has keeps track of every step you (and your smartphone) take. Your Google Timeline, introduced last year, can be a true walk down memory lane, but it can also lead straight…
Jigsaw ransomware deletes more files the longer you delay paying
Source: Computerworld Malware researchers have released a tool that can decrypt files affected by the new threat Understanding how to buy bitcoins and pay ransomware authors for decryption keys is hard enough, yet some cybercriminals now expect their victims to do it in under an hour if they want all of their files back. A…
Choosing the cloud that’s right for you
Source: Computerworld OPINION BY AL KUEBLER Not every organization has moved its IT operations to the cloud, nor should we expect that to be the case. There are legitimate reasons to adhere to the on-premises IT approach, not the least of which is the fact that it assures that your IT infrastructure and all the…
Don’t Let These HR Tech Horror Stories Happen to You
BY MICHELLE V. RAFTER Source: PC Mag Pierre Tremblay can’t undo April 29, 2015, the day someone on his human resources (HR) team accidentally sent a “You didn’t get the job” email to about 110 job applicants—including people the company wanted to hire. He can make sure it never happens again. Like that misdirected email,…
Banking Trojans Take Backseat to Ransomware
The banking trojan — a type of malware used to steal credentials for bank accounts — has been a staple of cyberthieves for years. However, ransomware, which has proven both easy to use and highly successful, has started eroding its popularity. In a typical banking trojan attack, a robber mounts a phishing campaign to entice…
New Windows 10 Upgrades Have A Nasty Surprise
Are you happy using Windows 7 or Windows 8? Would you like the Windows 10 upgrade? I’m asking you these questions for two reasons. Firstly because I think respecting consumer choice is important. Secondly because Microsoft’s latest Windows 10 upgrade trick demonstrates the company stopped caring about your answers to both these questions a long…
Kansas Heart Hospital hit with ransomware; attackers demand two ransoms
Credit: Shutterstock Kansas Heart Hospital was hit with a ransomware attack. It paid the ransom, but then attackers tried to extort a second payment. Kansas Heart Hospital in Witchita was hit with ransomware last week. The ransomware attack occurred on Wednesday, and the KWCH 12 news video from Friday night said some files were still…
The massive LinkedIn hack shows that people are awful at picking passwords
We know that many people are awful at picking passwords — and the huge hack of LinkedIn confirms it. The professional social network was breached back in 2012, but it has returned to the news this week as we finally learned the true scale of it: A whopping 167 million accounts were compromised, including 117…
Half the Web’s traffic comes from bots
Roughly half of all Web traffic comes from bots and crawlers, and that’s costing companies a boatload of money Strategies have changed dramatically in the past few years, with new approaches like consolidating your Read Now That’s one finding from a report released Thursday by DeviceAtlas, which makes software to help companies detect the devices…
Dell XPS 15 Review: A great laptop gets bigger and a little better
It doesn’t take a genius to realize that when you hit pay dirt, you might do so again if you keep digging in the same area. That’s the tack Dell takes with its redesigned XPS 15 laptop: It’s easily summed up as a bigger, more powerful version of the super-popular XPS 13. Bigger isn’t always…